Whonix 101: The Best Way to Use Tor
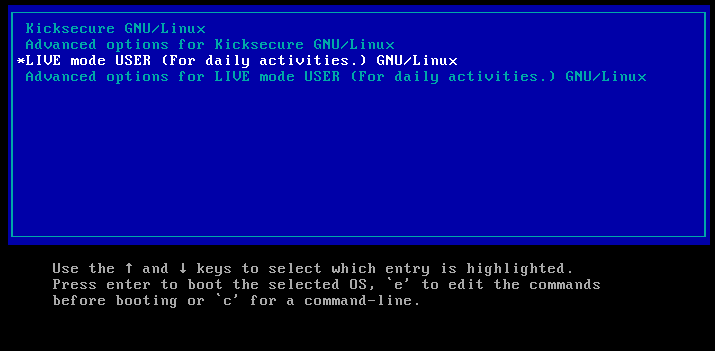
Whonix
Tor Browser is one way to use Tor. Another way is through the operating system Whonix in a virtual machine. There are 4 main security advantages of doing this. These are:
a) All Traffic is forced through Tor
b) Malware is contained in a virtual machine, preventing it from infecting the host
c) All of the traffic is routed through a 2nd virtual machine gateway if malware escapes the first virtual machine
d) The virtual machine’s operating system can be run in live mode, which means it erases all the contents after it’s done
Overview
Whonix is an operating system designed to be run in a virtual machine. It is among the most secure options available for browsing on Tor. All traffic by design is forced through Tor, which prevents leaks.
Based on Kicksecure
Whonix is based on Kicksecure, which is a security hardened version of Debian. There are two main differences between the original Kicksecure and Whonix, as follows:
a) On Whonix, all traffic is routed through Tor whereas on Kicksecure, it’s not.
b) Whonix uses two virtual machines – a workstation and a gateway. All internet browsing or activity is done in the workstation, and then this traffic is routed through the gateway before leaving to the internet. This is to prevent leaks.
In constrast, Kicksecure does NOT have a gateway.
How the Gateway Works
Whonix has the following structure:
You → Workstation → Gateway → Internet
The purpose of the gateway is to protect the user if malware escapes the first virtual machine. In addition, it provides a second layer of protection to force traffic through Tor and reduce the possibility of it escaping via clearnet access.
In practice, the chance of malware escaping both the workstation and gateway is incredibly rare. Also, this risk is reduced to virtually zero if JavaScript is completely disabled.
Live Mode
Both Whonix and Kicksecure offer a live mode option. When this is selected at each virtual machine boot up, all data is erased once the virtual machine is shut down. This ensures any malware, cookies, and tracking scripts will be destroyed once the browsing session is done. All internet browsing should be done in Live Mode. (The regular mode should be used only when Whonix or Kicksecure needs to be updated.)
Whonix’s non-persistent mode should ONLY be used for updating the operating system and potentially for updating software. It absolutely should NOT be used for regular internet browsing, as it’s unknown what cookies or scripts could be downloaded.
Downloading Software
Software can be installed on the Whonix virtual machine in regular mode so the software persists between sessions, but only if it is TRUSTED and is needed for every session. However, the user must use extremely good judgment in deciding what software can be trusted enough to persist inside Whonix, as doing so could compromise all browsing if the software is malicious.
We recommend exclusively using free and open source software if it is downloaded in persistent mode.
Make Clones for Software
If the user has enough memory on the direct hard drive or on external USB drives, then additional Whonix virtual machines can be set up as clones — each with unique persistent clone software, which could be configured for different purposes.
What defines Malware
When you say “malware,” people usually think of software that is installed. But malware could exist in a huge variety of forms. For example, a PDF could contain a malicious script to send back your IP address to its creator.
If you were to download a PDF from Tor Browser alone and run it outside of Tor Browser, the PDF could potentially report back your real IP address, whereas with Whonix, all traffic is routed through Tor. The PDF script would not be able to escape the virtual machine and would not be able to avoid being routed through Tor.
Conclusion
Are you feeling overwhelmed with the amount of technical knowledge required to properly set up and use virtual machines? At Simplified Privacy, our team is ready to help you with your Whonix and Kicksecure setups and cater advice to your specific needs.
We can dramatically improve the quality of your experience. Don’t make mistakes that expose your safety unnecessarily, or slow down your internet or computer with a bad setup. Your consultation would be end-to-end encrypted on easy to download and use apps like Signal, Session, or XMPP, for anonymous cryptocurrency.
If you really want to learn and take your privacy to the next level, subscribe to our new content via: Podcast RSS, Session list, Nostr, Bastyon, Article RSS, or join the Signal Group
Related Posts

Whonix Support for HydraVeil
Instructions for Whonix
[SP]
May 16, 2025

Tor Browser ends OS spoof
What's this mean for you?
[SP]
Apr 25, 2025
Tor & IPFS are opposites
Opposite Server Setups.
[SP]
Jul 20, 2024

Tor Onion Nostr Guide: Best Apps
Tor and Nostr together is amazing for censorship resistance. Let's go over some tools you can use to do this.
[SP]
Mar 26, 2024